Top security risk in DeFi: Cross-chain bridges are the most targeted


Unfortunately for investors, crypto heists are having a moment. The cross-chain Nomad bridge was exploited by a hacker and various other users, draining almost all of their total funds. Even though some users returned a small portion of the funds, the DeFi space is beginning to wonder why so many attacks have taken place in the last months.
Is it a coincidence that DeFi bridges are getting hacked on a regular basis? Could it be that their security systems are too easily breached by hackers? Blockchain data platform Chainalysis has released a report about the continuous attacks on space.
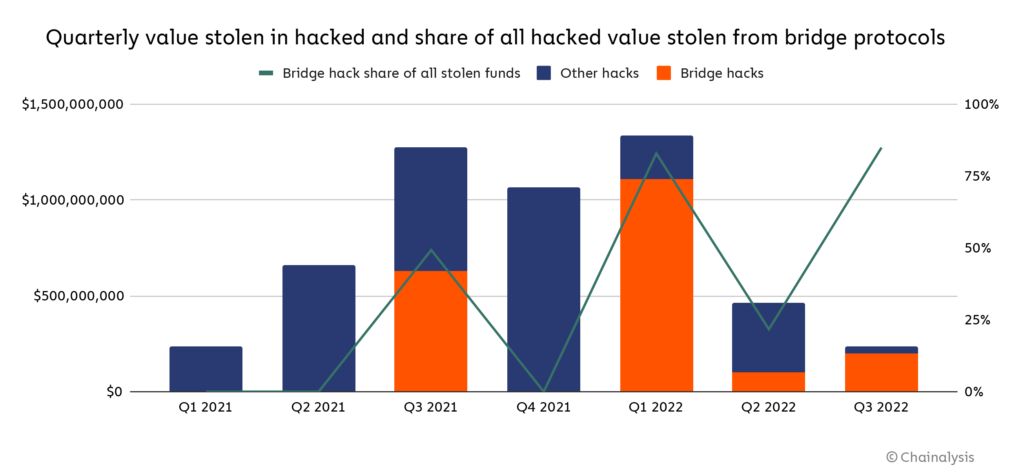
The company estimates that $2 billion worth of cryptocurrency was stolen from cross-chain bridges this year through 13 different hacks. And of the total amount of funds stolen this year, almost 70% came from attacks on cross-chain bridges.
Although this doesn’t bring confidence to users, there is hope to improve security systems thanks to the transparency and traceability of the blockchain. Stolen funds can be traced to prevent hackers from withdrawing the stolen gains.
Cross-chain bridges are widely used in DeFi because they allow users to exchange digital assets from one blockchain to another. This enables the flow of data that would not be allowed otherwise.
These bridges usually hold large amounts of liquidity deposited by users, making them an ideal target for hackers. Each protocol has its own bridge design, which is constantly being tested and upgraded. Clearly, these bridge designs present many technical problems.
What can be done?
Hackers will always be on the lookout for the most vulnerable targets. A few years ago, centralized exchanges were the targets. Today, it is rare to hear an exploit in such exchanges, as they prioritize security. This is what DeFi should be aiming toward. Rigorous code audits must take place for both developers building the protocols and investors evaluating them. Teams should also be up-to-date on hacking trends and receive proper training.
When the attack happens, immediate tracing and labeling of funds must occur to minimize the damage and prevent the attackers from cashing out the stolen funds.
Read related posts:
Disclaimer
In line with the Trust Project guidelines, please note that the information provided on this page is not intended to be and should not be interpreted as legal, tax, investment, financial, or any other form of advice. It is important to only invest what you can afford to lose and to seek independent financial advice if you have any doubts. For further information, we suggest referring to the terms and conditions as well as the help and support pages provided by the issuer or advertiser. MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice.
About The Author
Agne is a journalist who covers the latest trends and developments in the metaverse, AI, and Web3 industries for the Metaverse Post. Her passion for storytelling has led her to conduct numerous interviews with experts in these fields, always seeking to uncover exciting and engaging stories. Agne holds a Bachelor’s degree in literature and has an extensive background in writing about a wide range of topics including travel, art, and culture. She has also volunteered as an editor for the animal rights organization, where she helped raise awareness about animal welfare issues. Contact her on agnec@mpost.io.
More articles

Agne is a journalist who covers the latest trends and developments in the metaverse, AI, and Web3 industries for the Metaverse Post. Her passion for storytelling has led her to conduct numerous interviews with experts in these fields, always seeking to uncover exciting and engaging stories. Agne holds a Bachelor’s degree in literature and has an extensive background in writing about a wide range of topics including travel, art, and culture. She has also volunteered as an editor for the animal rights organization, where she helped raise awareness about animal welfare issues. Contact her on agnec@mpost.io.





















































