ZK-based Privacy Tech Stack Will Usher a New Era of Software, says Verida CEO Chris Were


In Brief
Chris Were, CEO of Verida emphasizes user control, encryption and use of zero-knowledge proofs to mitigate data breaches.

Today, there are growing concerns surrounding data breaches and privacy violations in centralized systems, which are complex, comprising numerous components and often involving thousands of employees with varying levels of access to data. Most hacks result from social engineering, primarily targeting employees.
This has led to the introduction of the privacy tech stack in the security landscape, offering enhanced control and protection for both individuals and businesses.
In a conversation with Metaverse Post – Chris Were, CEO of Verida highlighted the privacy tech stack represents a transformative force that can usher in a new era of software development where user control, data security, and privacy take precedence.
Verida is a full-stack development framework and decentralized personal data network for Web3.
“Picture a data breach in a centralized platform like a break-in where a hacker gains access to the entire system, compromising every user’s data. This is a significant issue, as one vulnerability exposes everyone’s information. However, in the emerging privacy technology stack, the data is decentralized, residing with individual users. Consequently, a security breach only affects one person, making the impact much more localized and manageable,” Chris Were told Metaverse Post.
“It’s important to note that a substantial portion of hacks stems from password theft. In the emerging privacy tech stack, passwords are phased out in favor of larger encryption keys and private keys, making them nearly impossible to crack. This shift, coupled with the elimination of passphrases and security questions, enhances overall security and privacy for end-users,” he added.
One of the key components of the privacy tech stack is decentralized identity and it ensures that a user’s personal information is secured and managed solely by the user, utilizing a private key unique to each user. This shift not only puts users in control but also sets the stage for secure and transparent digital interactions.
Role of Zero Knowledge Proofs in Privacy Tech Stack
Zero-knowledge proofs is a critical pillar in the privacy tech stack, enabling users to share only the necessary information required to access a service. This technology uses cryptographic methods, reducing the risk of exposing sensitive information and enhancing security by storing zero-knowledge credentials on decentralized databases.
Highlighting the impact, Chris Were said, “Today, when we share data, we have to share the actual information itself. For example, if I want to prove that I’m over 18 years of age, I will probably need to share with you a passport or a driver’s license, providing a significant amount of information about me just to prove my age.”
“A zero-knowledge credential, on the other hand, operates differently. It uses advanced mathematics and allows two parties to communicate, enabling me to prove to a third party that I’m over 18 without disclosing any actual information, not even my name,” he added.
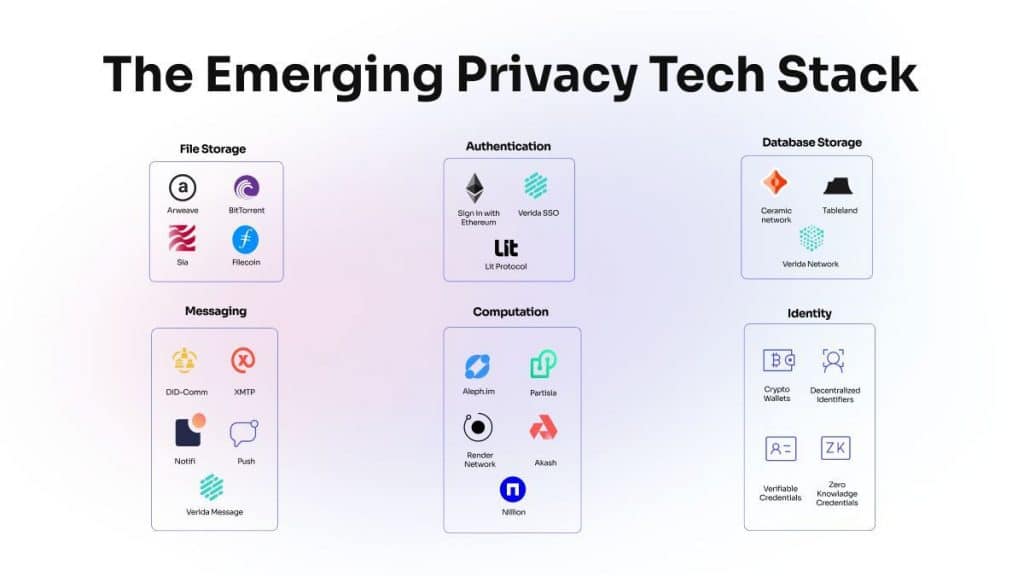
Yet another important element of the privacy tech stack is decentralized databases that have a unique capability to mitigate cybersecurity risks when compared to their centralized counterparts. The core of their strength lies in placing control directly in the hands of users through private keys, creating a fortress of security and privacy.
Unlike centralized databases that demand implicit trust in the company, decentralized systems operate on a user-centric model. In this paradigm, businesses and applications must explicitly seek user permission to access data, fostering a sense of confidence in data privacy. This approach stands in stark contrast to the prevalent issues of security breaches in centralized platforms, where a single breach can compromise the data of all users.
“We are already witnessing a growing awareness among users regarding the vulnerabilities their data faces on the internet, including the risks of hacking and data security breaches. This heightened awareness will prompt users to consciously consider the products and services they engage with,” said Verida’s Chris Were.
“Security is a fascinating aspect often overlooked until it becomes a problem. Forward-thinking companies are investing in migrating to this new decentralized model, seizing the opportunity to gain an edge over competitors who may face security breaches,” he added.
As applications proliferate, users increasingly recognize the value of data control. Demand for apps facilitating user data accessibility and utility is poised for growth.
Disclaimer
In line with the Trust Project guidelines, please note that the information provided on this page is not intended to be and should not be interpreted as legal, tax, investment, financial, or any other form of advice. It is important to only invest what you can afford to lose and to seek independent financial advice if you have any doubts. For further information, we suggest referring to the terms and conditions as well as the help and support pages provided by the issuer or advertiser. MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice.About The Author
Kumar is an experienced Tech Journalist with a specialization in the dynamic intersections of AI/ML, marketing technology, and emerging fields such as crypto, blockchain, and NFTs. With over 3 years of experience in the industry, Kumar has established a proven track record in crafting compelling narratives, conducting insightful interviews, and delivering comprehensive insights. Kumar's expertise lies in producing high-impact content, including articles, reports, and research publications for prominent industry platforms. With a unique skill set that combines technical knowledge and storytelling, Kumar excels at communicating complex technological concepts to diverse audiences in a clear and engaging manner.
More articles

Kumar is an experienced Tech Journalist with a specialization in the dynamic intersections of AI/ML, marketing technology, and emerging fields such as crypto, blockchain, and NFTs. With over 3 years of experience in the industry, Kumar has established a proven track record in crafting compelling narratives, conducting insightful interviews, and delivering comprehensive insights. Kumar's expertise lies in producing high-impact content, including articles, reports, and research publications for prominent industry platforms. With a unique skill set that combines technical knowledge and storytelling, Kumar excels at communicating complex technological concepts to diverse audiences in a clear and engaging manner.






















































