Cloudflare Breaks Records by Stopping the Largest DDoS Attack with Requests per Second Peaking at 71 Million

In Brief
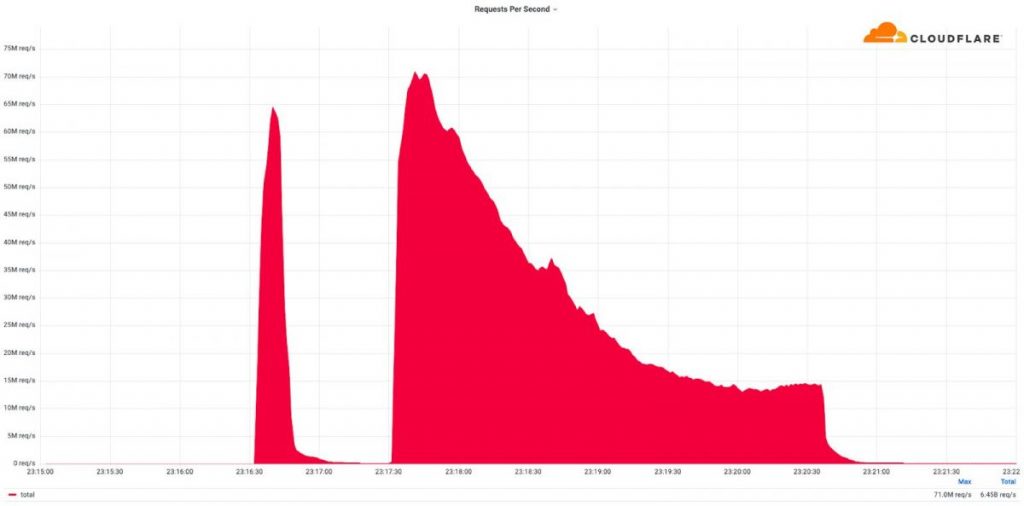
Cloudflare has set a new record in defending against a DDoS attack, which peaked at approximately 71 million requests per second over the weekend, targeting Cloudflare-protected websites.
Cloudflare revealed that most of the attacks originated from cloud providers and traced the attacks back to over 30,000 IP addresses.

Cloudflare has defended against a distributed denial-of-service (DDoS) attack that reached a new record of 71 million requests per second. The record-breaking DDoS attack surpassed the previously reported record of 46 million requests per second in June 2022 by 35%.
The attacks took place over the weekend and peaked at approximately 50 million to 70 million requests per second. These HTTP/2-based attacks targeted Cloudflare-protected websites and were traced back to over 30,000 IP addresses.
The DDoS-affected sites included a popular gaming provider, cryptocurrency companies, hosting providers, and cloud computing platforms. According to Cloudflare, “the attacks originated from numerous cloud providers.”
“Over the past year, we’ve seen more attacks originate from cloud computing providers,”
the company added.
Cloudflare will offer a free botnet threat feed to service providers with autonomous systems. The feed will provide threat intelligence about providers’ own IP spaces and the origins of attacks.
The internet infrastructure company claims that DDoS attacks have been increasing in size, sophistication, and frequency. In its latest DDoS threat report, Cloudflare observed a 79% yearly increase in HTTP DDoS attacks, a 67% QoQ rise in volumetric attacks exceeding 100 Gbps, and an 87% QoQ increase in attacks lasting over three hours.
The intention behind a DDoS attack is to impede the normal flow of traffic to a targeted network, server, or service by flooding the system or its surrounding infrastructure in a malicious effort. The objective of such cyberattacks is to disable internet properties and restrict user access. They are particularly potent against sites lacking adequate protection, requiring only minimal resources and expenses for the perpetrators to launch.
Related posts:
Disclaimer
In line with the Trust Project guidelines, please note that the information provided on this page is not intended to be and should not be interpreted as legal, tax, investment, financial, or any other form of advice. It is important to only invest what you can afford to lose and to seek independent financial advice if you have any doubts. For further information, we suggest referring to the terms and conditions as well as the help and support pages provided by the issuer or advertiser. MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice.
About The Author
Agne is a journalist who covers the latest trends and developments in the metaverse, AI, and Web3 industries for the Metaverse Post. Her passion for storytelling has led her to conduct numerous interviews with experts in these fields, always seeking to uncover exciting and engaging stories. Agne holds a Bachelor’s degree in literature and has an extensive background in writing about a wide range of topics including travel, art, and culture. She has also volunteered as an editor for the animal rights organization, where she helped raise awareness about animal welfare issues. Contact her on agnec@mpost.io.
More articles

Agne is a journalist who covers the latest trends and developments in the metaverse, AI, and Web3 industries for the Metaverse Post. Her passion for storytelling has led her to conduct numerous interviews with experts in these fields, always seeking to uncover exciting and engaging stories. Agne holds a Bachelor’s degree in literature and has an extensive background in writing about a wide range of topics including travel, art, and culture. She has also volunteered as an editor for the animal rights organization, where she helped raise awareness about animal welfare issues. Contact her on agnec@mpost.io.





















































