QR Code’ Surge in Popularity Brings Along a Rise in QR-Linked Phishing Scams


In Brief
Advancing image-based phishing further, threat actors have adopted QR codes in a trend called ‘Qishing’ to mask their malicious URLs.
Attackers are concealing harmful links within QR codes that mimic multi-factor authentication processes. Victims are enticed to scan these QR codes using their mobile devices for acces

With the global populace of smartphone users reaching an astounding 6.92 billion in 2023, approximately 86% of the world’s inhabitants now possess the means to unlock the contents concealed within QR codes — square repositories of encoded data easily decipherable by smartphones.
Enabled by their open-source character, QR code generators have now proliferated across the online realm. However, the surge in QR code proliferation has sparked heightened concerns regarding the rise of phishing attacks.
The accessibility and versatility of QR codes have positioned them as a prime tool for cybercriminals, who are currently exploiting their potential to hide malicious links and evade anti-spam filters.
Threat actors have been embedding images within phishing emails for a while now, concealing malicious code beneath these visuals. These images cleverly masquerade as genuine messages designed to deceive recipients.
Despite resembling typical phishing communications, these image-based messages contain significantly condensed HTML source code. This characteristic makes their identification through traditional filters, which depend on message content, much more challenging.
Often, only the detectable malicious URL is uncovered.
Advancing image-based phishing even further, threat actors have adopted QR codes in a trend called ‘Qishing’ to mask their malicious URLs.
Security services firm Trustwave SpiderLabs recently investigated this new trend and the different methods attackers use to trick their victims.
“Qishing enables attackers to hide their malicious URLs in the QR code. The samples we have observed using this technique are primarily disguised as Multi-factor Authentication (MFA) notifications, which lure their victims into scanning the QR code with their mobile phones to gain access,” Karl Sigler, manager of SpiderLabs Threat Intelligence at Trustwave, told Metaverse Post. “However, instead of going to the target’s desired location, the QR code leads them to the threat actor’s phishing page.”
Scanning QR Codes? Stay Alert and Informed
Cybercriminals are progressively integrating well-known technologies into their attack methods. Whether scanning restaurant menus or employing QR codes from apps like Venmo, users trust QR codes, often without skepticism.
“Trustwave SpiderLabs researchers observed Qishing attacks that targeted specific organizations with personalized templates. The goal is to make the recipient believe the email is legitimate. Using the victim’s organization logo or a business partner’s logo helps make the email more compelling,” Trustwave SpiderLabs’ Sigler told Metaverse Post.
Threat actors are tailoring their efforts to specific organizations, utilizing personalized templates that feature the victim organization’s logo to enhance authenticity.
“Attackers employ these techniques to decrease a user’s skepticism of the email. If it looks like a company email or an email from a well-known business, users will be quick to open it and click on it,” said Sigler.
Attackers are concealing harmful links within QR codes that mimic multi-factor authentication processes. Victims are enticed to scan these QR codes using their mobile devices for access.
Yet, instead of arriving at their intended destination, the QR codes redirect them to the phishing page orchestrated by the threat actor.
Malicious QR codes find a home within PDF attachments. These emails, preceding text content, encourage recipients to open attached PDF files housing the malicious QR codes.
“PDF documents are still trusted by many who expect to receive these attachments. Security controls like Secure Email Gateways may be able to inspect an Office document or even malicious content in a PDF,” Sigler told Metaverse Post. “However, since QR codes are just images, inspection will likely result in seeing a clean file.”
The email lacked body content in one email sample that Trustwave SpiderLabs researchers observed. Instead, it enticed recipients to open an attached PDF file harboring the malicious QR code. The inclusion of the PDF introduces an additional layer that enhances the email’s ability to evade anti-spam filters.
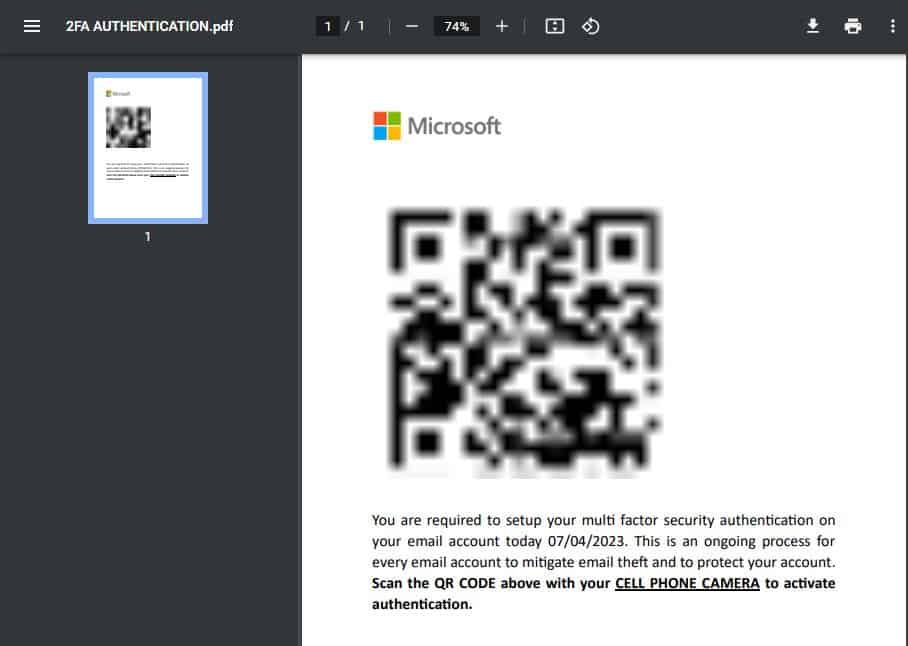
Likewise, some phishing emails include HTML attachments hosting QR codes. Once victims access the attached HTML file, they are prompted to scan the embedded QR code, leading them to a phishing page.
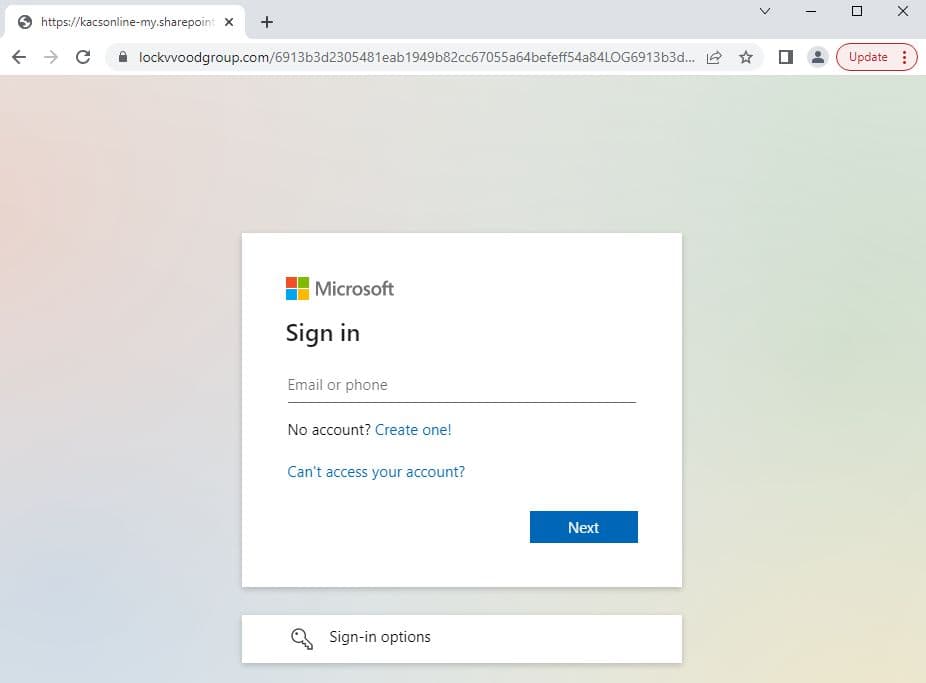
The QR codes are generated dynamically using APIs, such as those provided by qrserver.com, enabling attackers to tailor the content for each attack instance.
“Although these image messages appear visually like other phishing messages, the HTML source code underneath is much shorter. This makes it more challenging to detect via conventional filters that heavily rely on message content for blocking as fewer red flags are present, leaving only the malicious URL visible for detection,” explained Sigler.
Quishing Awareness And Risk Mitigation
To counter these evolving threats, heightened awareness and cybersecurity training are crucial.
“Raising awareness is key to protecting ourselves from these threats. Organizations should advocate training staff members to be more vigilant when inspecting unexpected emails and applying strong security measures to protect their network,” Trustwave SpiderLabs’ Sigler told Metaverse Post.
“I can’t think of a single valid reason a QR code should be embedded into an email outside of potentially an email signature. If you see a QR code in an email, do not scan it. This is especially true for emails where the sender specifically asks you to scan the code.”
Disclaimer
In line with the Trust Project guidelines, please note that the information provided on this page is not intended to be and should not be interpreted as legal, tax, investment, financial, or any other form of advice. It is important to only invest what you can afford to lose and to seek independent financial advice if you have any doubts. For further information, we suggest referring to the terms and conditions as well as the help and support pages provided by the issuer or advertiser. MetaversePost is committed to accurate, unbiased reporting, but market conditions are subject to change without notice.
About The Author
Victor is a Managing Tech Editor/Writer at Metaverse Post and covers artificial intelligence, crypto, data science, metaverse and cybersecurity within the enterprise realm. He boasts half a decade of media and AI experience working at well-known media outlets such as VentureBeat, DatatechVibe and Analytics India Magazine. Being a Media Mentor at prestigious universities including the Oxford and USC and with a Master's degree in data science and analytics, Victor is deeply committed to staying abreast of emerging trends. He offers readers the latest and most insightful narratives from the Tech and Web3 landscape.
More articles

Victor is a Managing Tech Editor/Writer at Metaverse Post and covers artificial intelligence, crypto, data science, metaverse and cybersecurity within the enterprise realm. He boasts half a decade of media and AI experience working at well-known media outlets such as VentureBeat, DatatechVibe and Analytics India Magazine. Being a Media Mentor at prestigious universities including the Oxford and USC and with a Master's degree in data science and analytics, Victor is deeply committed to staying abreast of emerging trends. He offers readers the latest and most insightful narratives from the Tech and Web3 landscape.





















































